Hacking sex toys…
Watch out, everyone. Your orifices are in danger.
Uncontrollable vibrations, mutations, and embarrassment. Oh my!
Or at least that’s what the current line of hacking projects are insinuating.
This is all in regards to a post that has the sex toy world in quite the kerfuffle. Specifically, a term called “Screwdriving” (Bluetooth hacking sex toys) which is used by the Pen Test Partners who make it a point to test the security of various products.
In this case, it was the Lovense HUSH.
Which in and of itself is an essential thing. Products should be pushed for as much consumer protection as possible and these kinds of tests point out possible flaws so companies can improve their designs.
But … (yes, you saw that coming)…
The scenario that was presented made me sigh – not to mention roll my eyes when I found out that some journalists gave us 2 HOURS (taking into account there’s a time difference between countries) to “respond” to their article before they published it. Bad form, people.
So, let’s sort out the bedlam and fear.
Does Lovense, as well as many competitors, use BLE (Bluetooth Low Energy) chips?
Yes. This is common in nearly all wearable or Bluetooth vibrators sex toys and the current industry standard as well as an upgrade over the older 3.0 version. The main reason for using this is (as the name states) to make sure the device doesn’t drain the battery as badly.
Are they 100% secure? No. Of course not.
No Bluetooth device is … because it’s Bluetooth.
BLE chips are meant for efficiency and as much security as the current technology allows.
This takes us to the next part…
Did they hack the Lovense Hush butt plug?
Yep. And boy did that make me sigh again.
Why?
Clear away all the coding images and language like “victim” and “unsafe”, what are you really left with?
A lot of missing information about the rest of the toy and app design as well as easy steps you can take to omit this possibility (if you’re that terrified of the concept).
#1. IT TAKES TIME AND RESOURCES
You need your BLE sniffing hardware (as PTP stated), which the average person doesn’t even know about.
The hacker also needs to study the Lovense protocols before they can send any commands to the toy (which can take quite a bit of time and a significant degree of experience).
#2. IF THE TOY IS ON AND CONNECTED, YOU’RE FINE
Hackers would need to walk/drive around the city hoping someone has a teledildonic toy that is on but NOT connected to any phone.
It’s rare to encounter this situation because if a user is wearing it out of the house it needs to be connected to the app in order to function, and that’s the entire purpose of wearing it outside.
And if it’s on and connected to your phone, the hacking can’t happen because it can only be controlled by one device at a time, aka the phone you’re connected to.
#3. PROXIMITY IS EVERYTHING
First, you have to be 30 feet (10 meters) or less with a clear line of sight – Bluetooth signals don’t travel through obstacles well, things like walls … or thick clothes while sitting in a chair.
Second, if they move, you have to follow them and hope they don’t go in another room.
#4. STILL SCARED OF THE IDEA OF HACKING?
The whole ordeal seems to revolve around having it inside you and buzzing without your permission. And I can completely understand how that would scare off people and feed into some pretty hefty fearmongering.
The solutions are simple:
- If it’s in the bag, the power is off and can’t be hacked
- If the toy is on and in your bag, turn it off
- If you’re going to wear it outside, make sure it’s connected to the app
- If you’re wearing it at home, remember Bluetooth signals are crap through walls. They would need to sit right outside your window. And, if you’re wearing it at home, it should be connected to your phone anyway.
PTP article excerpt:
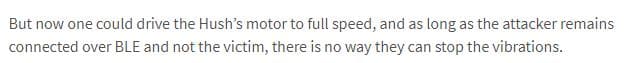
Sorry, guys. This is inaccurate.
If, somehow, it actually gets hacked*, just go to the bathroom, turn it off then on again, and then connect it to the app so no one else can control it.
Then go outside, find the person, and kick their ass for being a pervert.
*Anyone with the skills to hack beyond that (specifically while it’s connected) will not be interested in a sex toy, more likely something with a bank account attached to it.
WHAT’S ALL THE HUBBUB, BUB?
My point is, out of all the things to worry about, a vibrating toy would be low on the list. If someone took control, it wouldn’t drain your retirement fund or send nudes to your boss and co-workers. It would just buzz.
My concern with BLE’s would be…
Heart monitors, industrial monitoring sensors, geography-based targeting promotions (iBeacon), and other devices that could cause serious damage. They also mentioned sex toys that can give video feedback, and I agree stuff like this needs next level security.
But out of all the things to get worked up over… butt plugs…?
Really?
To “hack” a vibrating sex toy and then insinuate is a “serious breach of security” is like picking the lock on your parents’ bedroom and them turning it into the Pentagon.
With any technology, if someone wants it bad enough, they will find a way, and those people want way more than to make your sex toy buzz.
I’ll also add one final observation.
PTP article excerpt:

The PTP testers went outside and magically happened to find a toy that was on, but not connected to a phone, and in seriously close range?
Not to mention that Lovense has zero biometric data or sensors, so there is no way to know it was IN someone.
It’s all a little more than suspect.
Good for article traffic, but suspect.
. . . . . . . . . . . . . . . . . . . . .
Lovense works work with current technologies to make things as secure as possible, but we also need to make things simple and convenient for users.
So relax, turn on your toy, and enjoy the vibrations YOU control.